trust
Your Data is Secure With Rhombus
A better security platform from a team you can trust. Learn how partnering with Rhombus improves cybersecurity and sets your organization up for long-term success with secure-by-default architecture.
The Trusted Choice
Security Overview
Secure-by-Default Architecture for Total Peace of Mind
With decades of cybersecurity experience, our team of experts follow a security-first approach from design to engineering. We use ‘Zero Trust’ architecture that protects at every layer from the ground up.
Security That’s Built in to Your Solutions
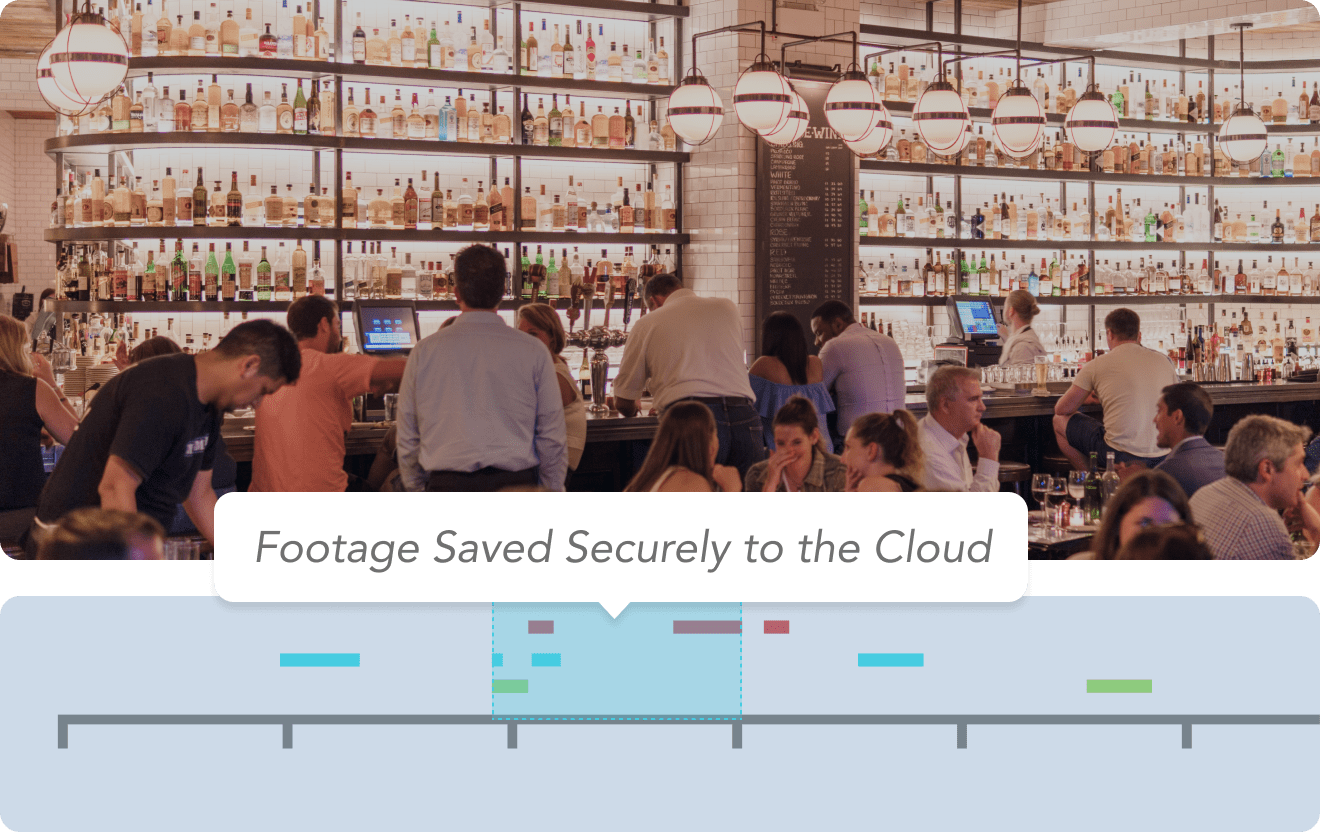
End-to-End Encryption
All media, video, and cloud communication is fully encrypted at rest and in transit, giving you total security and protection against man-in-the middle attacks. The system segregates and rotates all encryption keys, so that even if one key is compromised, all others remain secure.
![End-to-End Encryption]()
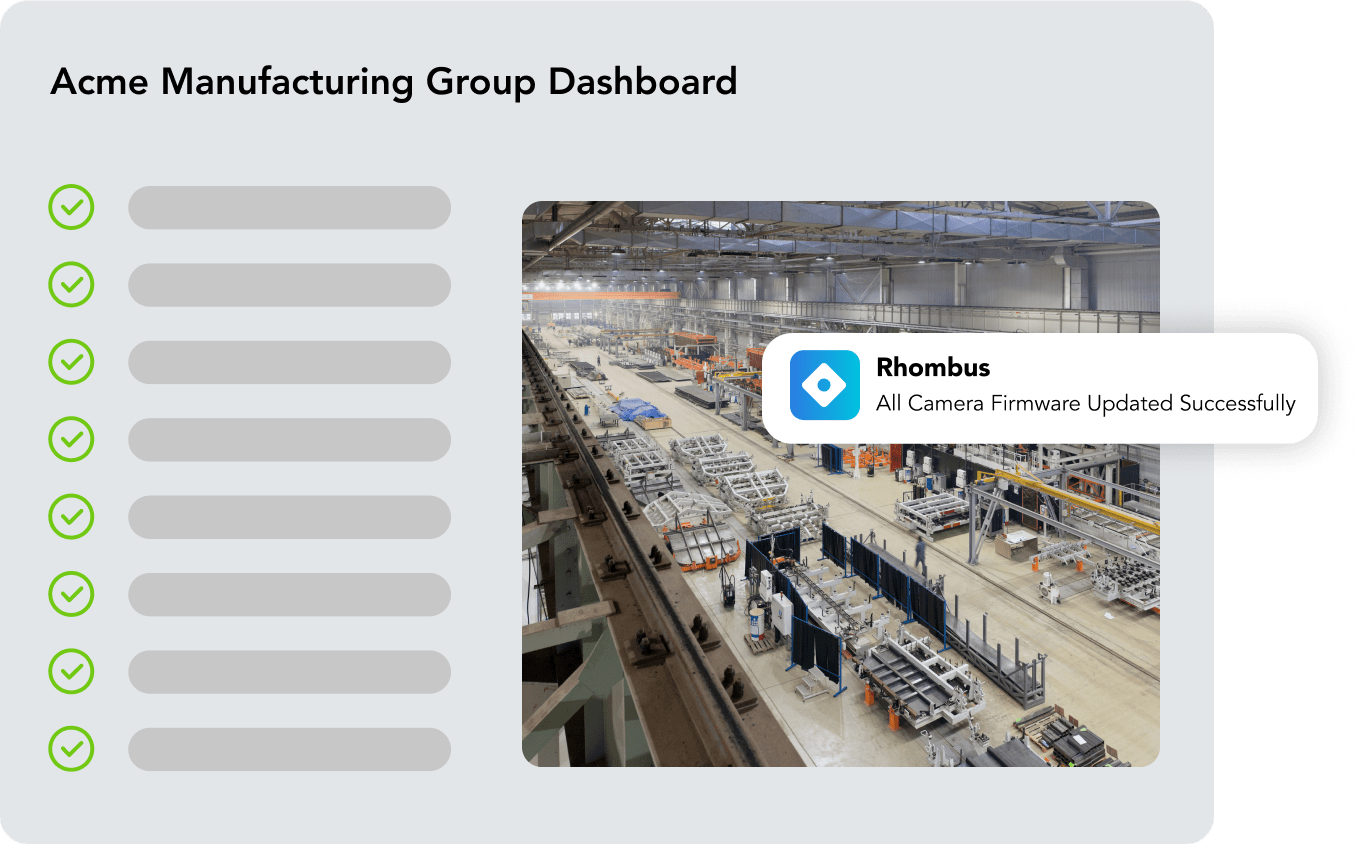
Automatic Security Updates
Firmware updates happen automatically, ensuring that you’re always 100% current with the latest cybersecurity protections. Automatic health monitoring catches potential issues before they develop, and regular third-party audits provide an added layer of protection.
![Automatic Security Updates]()
Hardware Security
All Rhombus devices are engineered in-house, and we use 100% whitelisted manufacturers who meet NDAA and TAA compliance. We design all devices from the ground up to be durable and reliable, and back our hardware with an industry-leading 10-year warranty.
![Hardware Security]()
DATA PRIVACY OVERVIEW
Manage, Protect, and Share Your Data with Complete Control
When data privacy truly matters, Rhombus has your back. We safeguard your data so you can enjoy complete security and peace of mind.
Built-In Data Privacy Protection
- Access Protocols
- Granular Permissions
- Secure Sharing
- SSO & 2FA
- Access Logs
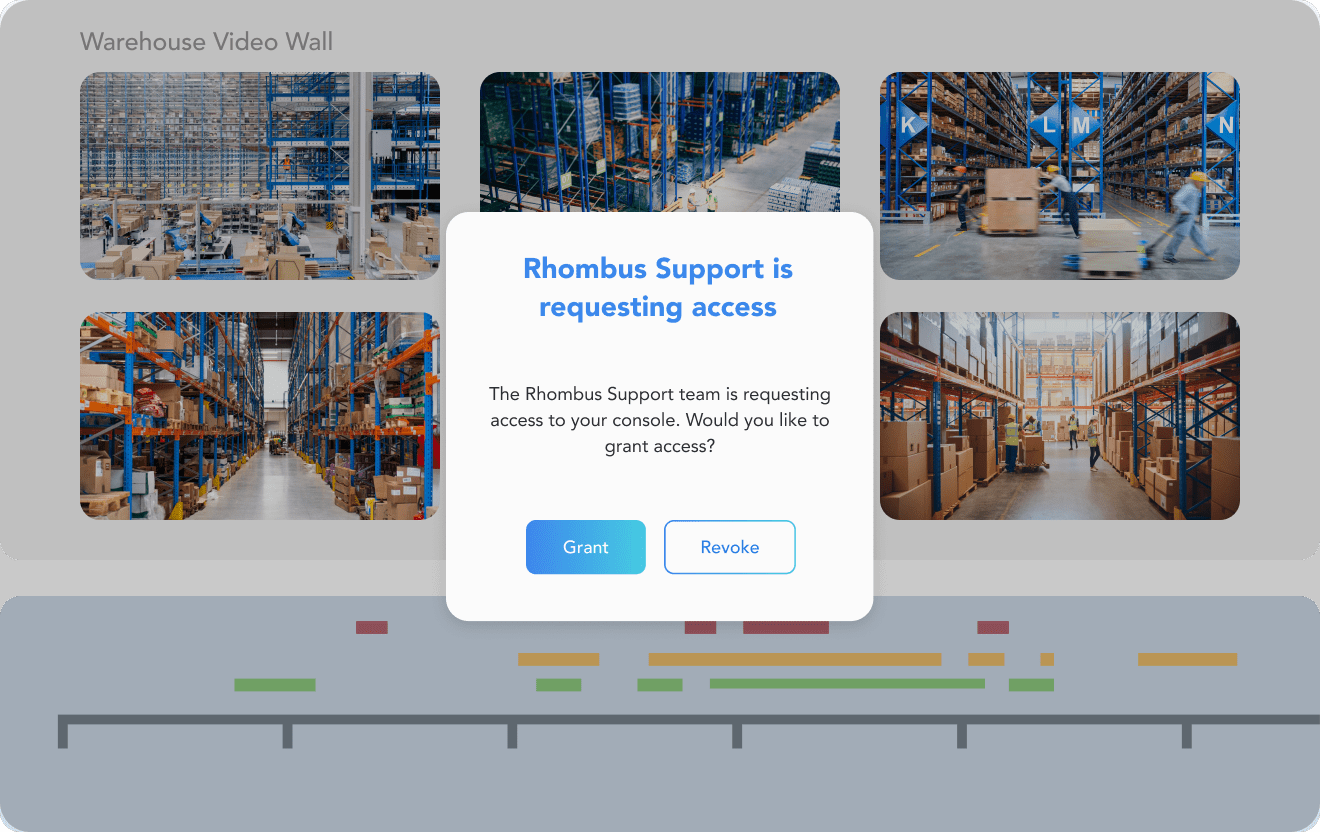
CONTROL SYSTEM ACCESS
Strict Access Protocols
Only you control and share access to your data—no exceptions. System access must be explicitly granted to Rhombus employees: there is no ‘super admin’ mode. No one except for authorized end users at your organization have the authority to initiate and provide account access to Support or Partners.
COMPLIANCE OVERVIEW
Effortlessly Stay Up to Date with Best Practices and Regulations
Rhombus adheres to strict cybersecurity and data privacy regulations, ensuring that your system is protected to the fullest extent of modern technology and industry best practices.
Rhombus Adheres to Enterprise-Grade Security Protocols

National Defense Authorization Act (NDAA)
All hardware procured from white-listed manufacturers for cybersecurity purposes.

Trade Agreements Act (TAA)
Hardware sourced exclusively from white-listed countries for cybersecurity purposes.

System and Organization Controls 2 Type 1 (SOC2 Type 1)
Framework demonstrating internal security processes to ensure data security.

System and Organization Controls 2 Type 2 Data Centers (SOC2 Type 2)
Security policies for service providers that store customer data in the cloud.
Maintain Compliance with Industry & International Regulations

Health Insurance Portability and Accountability Act (HIPAA)
Maintain HIPAA compliance using Rhombus as a tool to ensure the protection of PHI.

General Data Protection Protection Regulation (GDPR)
Stay in full compliance with GDPR data processing agreements.

Payment Card Industry Compliance (PCI)
Meet PCI standards by protecting cardholder data and sensitive authentication data.

Biometric Information Privacy Act (BIPA)
Comply with BIPA regarding the collection and storage of biometric information.

Personal Information Protection and Electronic Documents Act (PIPEDA)
Meet PIPEDA regulations on how businesses collect, use, and disclose such data.
Cybersecurity Maturity Model Certification (CMMC)
Comply with DoD cybersecurity standards for defense industrial base (DIB) contractors.

National Institute of Standards and Technology (NIST)
Comply with the strictest cybersecurity & data privacy standards in the US.

Criminal Justice Information Services (CJIS)
Adhere to standards set by criminal justice and law enforcement for securing CJI data.
See Rhombus for Yourself
Request a demo with our team today and see why industry leaders choose Rhombus
Request Demo